04. Threat Assessment Fundamentals
Threat Assessment Fundamentals
ND545 C3 L1 A04 Threat Assessment Fundamentals
Introduction to Threat Assessment
Cybersecurity breaches happen when a threat is able to successfully exploit a vulnerability within a business. To avoid attacks, security professionals must understand these factors and how they contribute to security failures. After this lesson, you’ll be able to explain the relationship between threats, threat actors, vulnerabilities, and exploits. You’ll also understand the threat assessment lifecycle.
The number of cyber threats to organizations is limitless. From hackers looking to steal data, to a flood that destroys data on computers, there are a variety of threats companies worry about. In addition, all threats are not created equally. Some are worse than others. Some don’t matter at all. Threat assessment is the process that helps organizations navigate the complex and dynamic world of cybersecurity threats.
Threat assessment is a subset of the overall risk management process. Before doing a threat assessment, you must understand the environment, inventory assets, know what’s important to the company.
Threat Assessment Process Summary
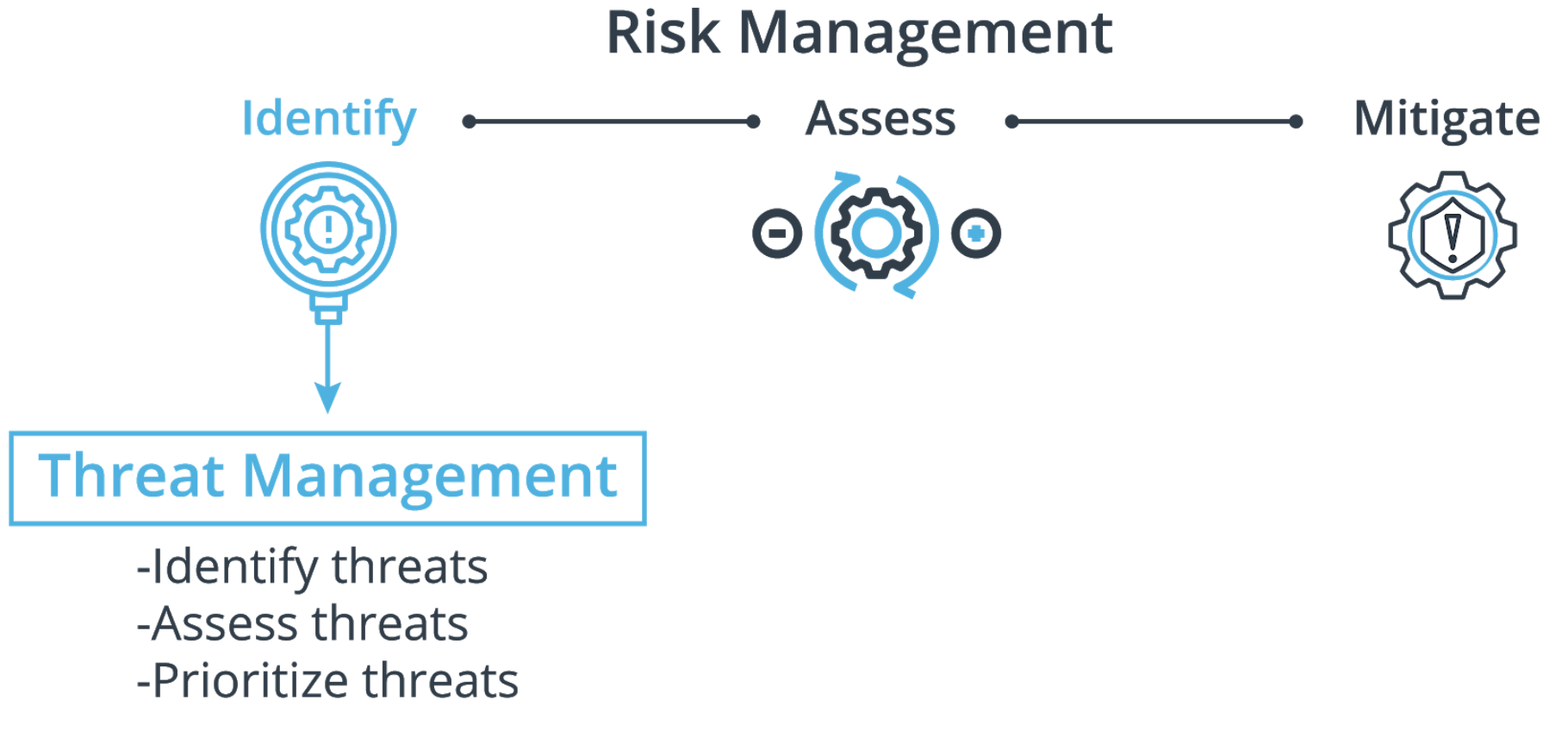
Threat Assessment Process Summary
The threat assessment process includes three key steps:
- Identify which threats are relevant to the organization.
- Assess the threat and how it might apply to or impact the organization.
- Prioritize which threats matter most based on what is important to the organization.
The ultimate goal of a threat assessment is to begin answering the following questions:
- What are the relevant threats that could impact the organization's information technology assets?
- Which threats represent the gravest danger to the company?
- Which threats have the greatest likelihood of leading to a successful negative outcome?
- Is the organization prepared to mitigate the threats? If not, what actions should be taken to mitigate the threat?
New Terms
To begin understanding threat assessment, here are fundamental terms to know:
• Threat: Any circumstance or event with the potential to adversely impact organizational operations (including mission, functions, image, or reputation), organizational assets, or individuals through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service. Also, the potential for a threat-source to successfully exploit a particular information system vulnerability.
• Threat assessment: Process of formally evaluating the degree of threat to an information system or enterprise and describing the nature of the threat.
• Vulnerability: Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source.
• Exploit: A code, tool, or mechanism that takes advantage of a vulnerability in a system in an attempt to breach security.
• Attack: Any kind of malicious activity that attempts to collect, disrupt, deny, degrade, or destroy information system resources or the information itself.
• Controls: A safeguard or countermeasure prescribed for an information system or an organization designed to protect the confidentiality, integrity, and availability of its information and to meet a set of defined security requirements.
• Risk: The level of impact on organizational operations (including mission, functions, image, or reputation), organizational assets, or individuals resulting from the operation of an information system given the potential impact of a threat and the likelihood of that threat occurring.
Definitions from the NIST CSRC Glossary: https://csrc.nist.gov/glossary